Only allow specific DHCP servers within your Layer 2 Broadcast Domain with the NSX DFW
I just came back from a customer who had a specific requirement.
Editing Only allow specific DHCP servers within your Layer 2 Broadcast Domain with the NSX DFW
The problem
The customer is afraid that someone is able to place a (rogue) DHCP server on the network. The placement can be done by creating a new virtual machine and make this machine a DHCP server, but also activate/install a DHCP server on an existing Virtual Machine.
The requirement
From the problem, a technical requirement was formed. The DHCP service should only be offered by specific and selected DHCP servers for specific segments.
Additional information
A DHCP server can offer services on its own local L2 segment, but also for a remote L2 segment (which makes it L3). When you please a DHCP server on another L3 segment you need to specify a DHCP helper/relay. When this helper/relay is not specified clients will not be able to request an IP address.
The theory
A typical DHCP operation consists of a few stages (DORA).
- Discovery - the client broadcasts a message on the local network segment its connected to, to discover available DHCP servers.
- Offer - a suitably configured DHCP server receives a request from a client and offers it an address from its pool of available addresses.
- Request - The client replies to the offer, requesting the address received in the Offer.
- Acknowledgment - The server acknowledges the request, marking the address as used in its pool of addresses, and informs the client of how long the address lease is valid for, and any other information needed.
Any device on a network segment can be a DHCP server. It doesn't have to be the router or the domain controller or any other "special" device on the network.
When the devices on your network first request an IP address or reach the end of their leases (or you force them to check their lease is still valid) they will simply broadcast a request for a DHCP server and will accept an offer from the first DHCP server to reply. This is important to remember as we look at the options for multiple DHCP servers.
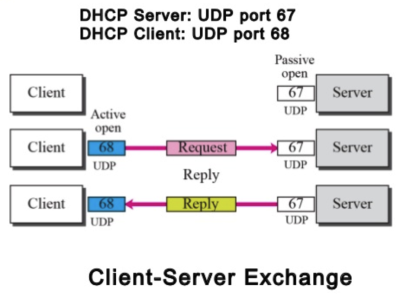
The DHCP client typically communicates with UDP port 68 and the DHCP server communicates with UDP 67. The direction of the communication is very important to know for the proposed solution.
The solution
By default the NSX Distributed Firewall has the following rules:
This translates into the following table:
| Name | Source | Destination | Service | Action | Apply To |
|---|---|---|---|---|---|
| Default Rule DHCP | Any | Any | DHCP-Client + DHCP-Server | Allow | Distributed Firewall |
| Default Rule | Any | Any | Any | Block | Distributed Firewall |
When we take a better look at the two service objects that are used in the "Default Rule DHCP” rule we see that they are specified like this:
DHCP-Client
DHCP-Server
Make a mental note that both service groups are using DESTINATION ports. This is important when we try to allow specific DHCP servers in our network.
When we turn the "Default Rule DHCP” off:
Turn the default rule off:
And look at the Live Flow Flow Monitoring for DHCP
We see that the SOURCE IP is set to 0.0.0.0 and the DESTINATION IP is set to 255.255.255.255. This makes it hard to specifically deny/allow DHCP servers in our network.
The only way how to solve our problem is to only allow the communication that is sent FROM the DHCP Server towards the client and blocks all other communication that is DHCP Server related for everyone.
This is achieved by the following rules:
This translates into the following table:
| Name | Source | Destination | Service | Action | Apply To |
|---|---|---|---|---|---|
| Allow specific DHCP Server(s) | DHCP-Server-02 | Any | UDP/67/SRC | Allow | LS-DHCPTEST |
| Deny all other DHCP Server(s) | Any | Any | UDP/67/SRC | Block | LS-DHCPTEST |
| Default Rule DHCP | Any | Any | DHCP-Client + DHCP-Server | Allow | Distributed Firewall |
| Default Rule | Any | Any | Any | Block | Distributed Firewall |
Because we specifically block the DHCP server traffic that is using UDP and UDP is stateless it uses UDP/67 as its SOURCE port (and not as its DESTINATION port, like the pre-configured "DHCP Server” service). So in order to make this work we need to create the following service and use this service in our own self-created Firewall Rules.
The testing
Below you will find the demo environment topology where I have tested this, with the testing steps and results.
In order to test the functionality I have created the below steps:
- Make sure DHCP-SERVER-01 and DHCP-SERVER-02 are both up and running and have the DHCP scopes activated
- Boot up DHCP-CLIENT-03
- The Client should get an IP address from one DHCP server
- Verify this at the DHCP server
- Release the IP address of the client
- Verify this at the DHCP server
- Deactivate the DHCP server scope that initially gave out the IP address
- Renew the IP address of the client
- The Client should get an IP address from the other DHCP server
- Verify this at the DHCP server
- Release the IP address of the client
- Verify this at the DHCP server
- Deactivate the DHCP server scope that lastly gave out the IP address
- Activate the other DHCP server scope again
- Renew the IP address of the client
- The Client should get an IP address from the DHCP server only alive
- Release the IP address of the client
- Verify this at the DHCP server
- Activate the other DHCP server scope again (make sure BOTH DHCP servers are activated now)
- Implement Distributed Firewall Rules with custom created service
- Make sure DHCP-SERVER-01 is only allowed
- Renew the IP address of the client
- The Client should get an IP address from DHCP-SERVER-01
- Verify this at the DHCP server
- Release the IP address of the client
- Verify this at the DHCP server
- Deactivate DHCP-SERVER-01 scope
- Renew the IP address of the client
- The Client should not get an IP address
- Only DHCP-SERVER-02 is active but this should be blocked by the Distributed Firewall
- Activate DHCP-SERVER-01 scope again
- Change the Distributed Firewall rule to only allow DHCP-SERVER-02
- Renew the IP address of the client
- The Client should get an IP address from DHCP-SERVER-02
- Verify this at the DHCP server
A video of the test results can be found here: